The platform builds threat models based on massive data, enabling full-process risk management from data collection, analysis, and warning to response, ensuring real-time vehicle driving cybersecurity. It offers vehicle cybersecurity situational awareness monitoring systems and solutions, or custom enterprise-level solutions and development services, ensuring visibility, management, control, and trust in automotive network security.
The platform integrates operations and maintenance services, analyzes and evaluates monitored data on anomalies and attack events in automotive networks, formulates emergency response and handling strategies, updates cybersecurity policies, and enhances the protection capabilities of the entire vehicle network system.
Product Features
Data Collection and Processing: Collect, filter, classify, and standardize multi-source data from vehicles and the cloud to create valuable insights.
Alert Detection and Analysis: Utilize threat models and AI technologies to detect logs in real time, issue alerts, and provide analytical tools to assess risks.
Risk Handling and Response: Offers highly automated and configurable processes and response plans, assigning and notifying responsible personnel to address issues.
Security Knowledge Base: Manages vulnerabilities, intelligence, regulations, and professional security knowledge, integrating them into the security analysis process to enhance threat detection and handling.
Vulnerability Management and Repair: Supports vulnerability scanning and manual reporting, assessing risks, and tracking repair progress.
Security Reports: Supports customizable time frames and statistical indicators, generating report templates for different reporting scenarios.
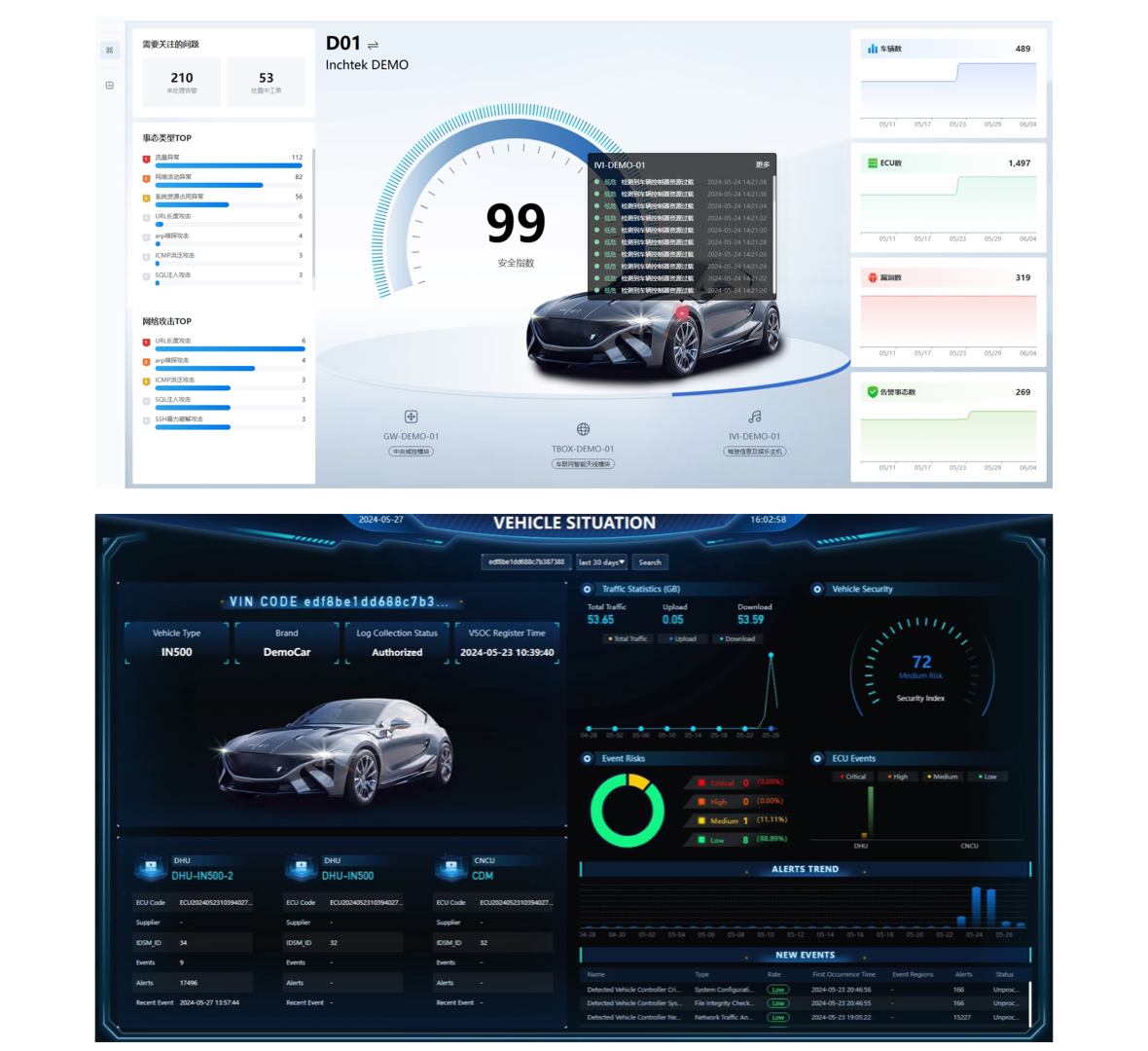
Situational Overview: Provides multidimensional views of asset risks and security protection levels, offering real-time alerts and tracking the progress of their resolution.
Policy Protection: Manages policy rules and deploys them to vehicles, tracking current versions and upgrade progress.
Product Architecture

Product Advantages
The integrated dashboard displays key indicators and architecture views, allowing users to monitor vehicle security in real-time and respond quickly.
Builds digital twin models of vehicle architectures, ECUs, firmware, and components, offering comprehensive security monitoring perspectives and precise risk identification and response capabilities.
Offers a wealth of analysis operators, supports custom scenario-based operator orchestration, and provides high-performance real-time processing, enhancing log analysis efficiency and reducing operational costs.
Uses generative AI to provide data insights, alert auxiliary analysis, and security Q&A functions, accelerating investigations and responses, and efficiently addressing operational challenges.
Covers the entire vulnerability lifecycle, supporting vulnerability scanning and reporting, and offering various risk assessment models and vulnerability databases to assist enterprises in building vulnerability management capabilities.
Provides low-code process orchestration, with built-in automated workflows for incident handling and vulnerability repair, integrating with rich applications and effectively aligning with enterprise CSMS processes.
Rich experience in overseas deployment and operations, fully compliant with GDPR, supports multiple languages, and enables rapid overseas deployment.